Egghunters in Exploit Development
What are Egg Hunters?
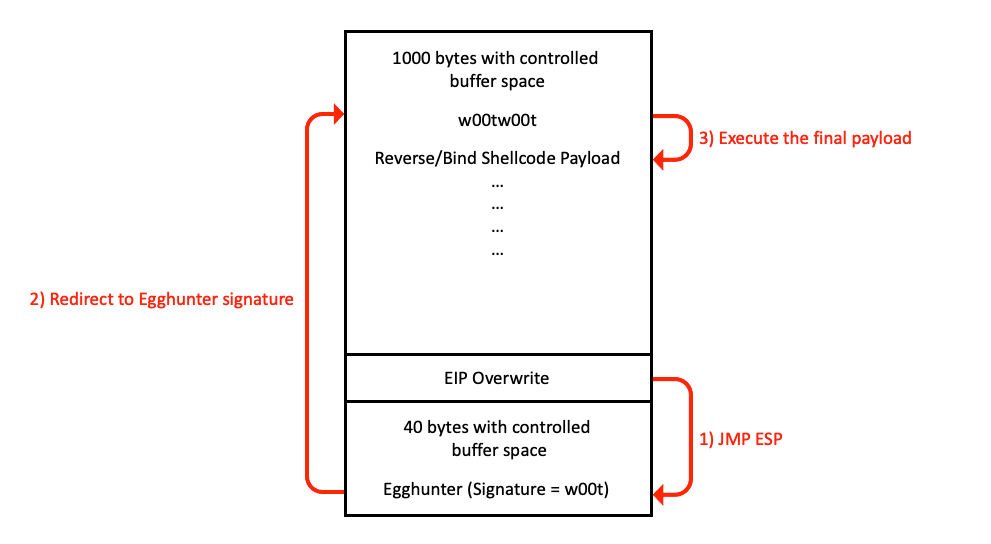
Egg Hunters are a specialized technique in exploit development used when the space for a payload is severely limited.
They enable the execution of larger payloads by searching through the process’s memory space to find a pre-defined code sequence (the ‘egg’) and then executing the subsequent payload (the ‘shellcode’).
How Do They Work?
The typical operation of an egg hunter includes the following steps:
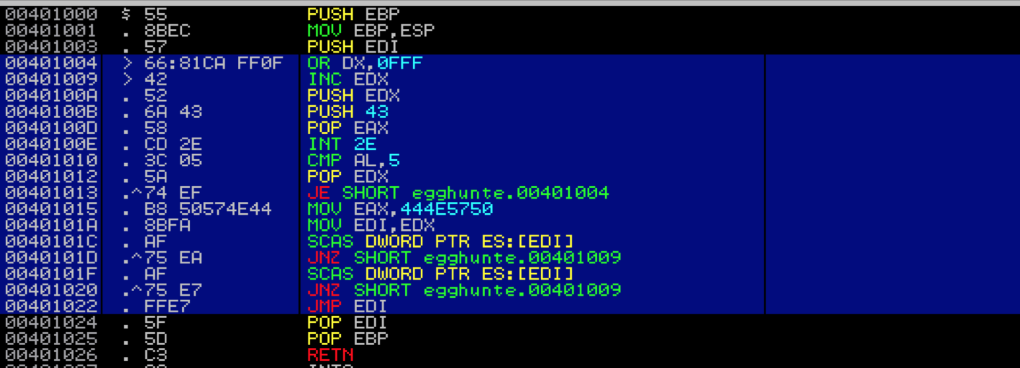
Initialization: The egghunter starts by setting up the necessary environment. This includes initializing registers and defining any constants or markers (‘eggs’) it will search for. For instance, the register EDX might be used to traverse through memory, and EAX might hold the egg to look for.
Memory Scanning: The egghunter then enters a loop where it scans the memory. It often checks memory page by page to avoid accessing restricted memory areas, which would cause exceptions or crashes. The egghunter might use system calls or certain instructions to ensure the memory address it is about to scan is accessible. For example, it might use an instruction like or dx, 0x0fff to align EDX to a memory page boundary and add edx, ebx to move to the next page.
Egg Checking: As it scans each memory page, the egghunter looks for the specific egg pattern. This pattern is a unique sequence of bytes that marks the start of the payload. The egghunter uses assembly instructions to compare memory content with the egg pattern. For example, it might use scasd (scan string doubleword) to compare the value in EAX (which holds the egg) with the value at the memory address pointed to by EDI.
Transfer Control: Once the egg is found, the egghunter needs to transfer control to the payload that follows the egg. This is typically done by jumping to the memory address where the egg (and hence the payload) is located. An instruction like jmp edi might be used, where EDI points to the location of the egg.
Here’s a slightly more detailed example, keeping in mind it’s a high-level overview:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
; Initialize registers
xor edx, edx ; Clear EDX register
mov eax, 0x77303074 ; Move the egg into EAX
; Memory Scanning Loop
start_scanning:
or dx, 0x0fff ; Align EDX to the next memory page boundary
add edx, ebx ; Move to the next page
push edx ; Save page address
push 0x2 ; System call number for access check
pop eax ; Load syscall number into eax
int 0x2e ; Call kernel to check access
cmp al, 0x05 ; Check if page is accessible
pop edx ; Restore page address
jz start_scanning ; If inaccessible, jump to next page
; Egg Checking
mov edi, edx ; Point EDI to current page
scasd ; Compare DWORD at EDI with EAX
jnz start_scanning ; If no match, jump to next page
scasd ; Check next DWORD
jnz start_scanning ; If no match, jump to next page
; Transfer Control
jmp edi ; Jump to the payload
In this example, the egghunter is looking for a specific egg (0x77303074 or w00t in ASCII) in the process’s memory.
When it finds this egg, it jumps to the payload to execute it.
Detecting Egg Hunters
In the context of exploit development, identifying egg hunters involves several key strategies. These strategies are crucial for understanding how egg hunters operate and detecting their presence in a system. Here’s a detailed look at these strategies:
Behavioral Analysis: This involves observing the unique memory scanning behaviors characteristic of egg hunters. Egg hunters typically search through memory for a specific pattern, or ‘egg’, indicating the start of a payload. By monitoring for unusual patterns of memory access, which differ from normal application behavior, you can potentially identify the presence of an egg hunter.
Signature-Based Detection: This method uses known patterns or signatures of egg hunter code within security tools. Since egg hunters have a specific structure and operational method, security tools can be configured to detect these unique signatures. This approach is akin to how antivirus programs detect known malware by their signatures.
Anomalous Activity Monitoring: This strategy involves identifying abnormal memory access patterns that might be induced by egg hunters. Since egg hunters scan through memory in a methodical and predictable manner, this can result in access patterns that are atypical for regular application behavior. Monitoring systems can flag these patterns as potentially malicious activities.
These strategies, when used effectively, can help in identifying and mitigating the risks posed by egg hunters in exploit development scenarios. By understanding these strategies, security professionals can better prepare and defend against attacks that utilize egg hunters.
Crafting an Egg Hunter
Crafting an egg hunter in exploit development involves a few essential steps to ensure its effectiveness and efficiency:
Compact Size: The egg hunter code needs to be as small as possible, so it fits into limited spaces within the target application without causing issues.
Efficient Memory Scanning: The egg hunter should scan through memory effectively and quickly to find the specific marker indicating the payload’s location.
Handling Errors: It’s crucial for the egg hunter to handle any potential errors, like memory access violations, to prevent crashing the process it is running in.
Mitigation Strategies
To mitigate the risks associated with egg hunters in exploit development, consider these strategies:
Memory Randomization: Use ASLR to randomize memory addresses, making it harder for egg hunters to find their payloads.
Execution Prevention: Implement DEP to prevent execution of code in non-executable memory segments, reducing the risk of payload execution by egg hunters.
Intrusion Detection: Deploy IDS/IPS systems to detect and block activities typical of egg hunters, like unusual memory access patterns.
These measures collectively enhance security against the threats posed by egg hunters. For further details on these strategies, exploring security-focused resources and literature on cyber defense is advisable.
Resources
- The Basics of Exploit Development 3: Egg Hunters: https://www.coalfire.com/the-coalfire-blog/the-basics-of-exploit-development-3-egg-hunters
- Exploit writing tutorial part 8 : Win32 Egg Hunting: https://www.corelan.be/index.php/2010/01/09/exploit-writing-tutorial-part-8-win32-egg-hunting/
- WoW64 Egghunter: https://www.corelan.be/index.php/2011/11/18/wow64-egghunter/
- Windows Exploit Development – Part 5: Locating Shellcode With Egghunting: https://www.securitysift.com/windows-exploit-development-part-5-locating-shellcode-egghunting/