Kerberos in Active Directory
Introduction
Kerberos is a cornerstone of authentication within Active Directory (AD), employing secret-key cryptography to secure client/server applications.
This protocol is essential for ensuring secure and efficient authentication across a network, particularly in AD environments developed by Microsoft for Windows domain networks.
How Kerberos Works
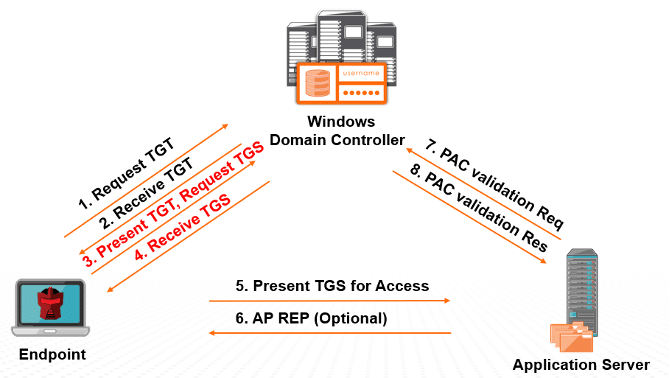
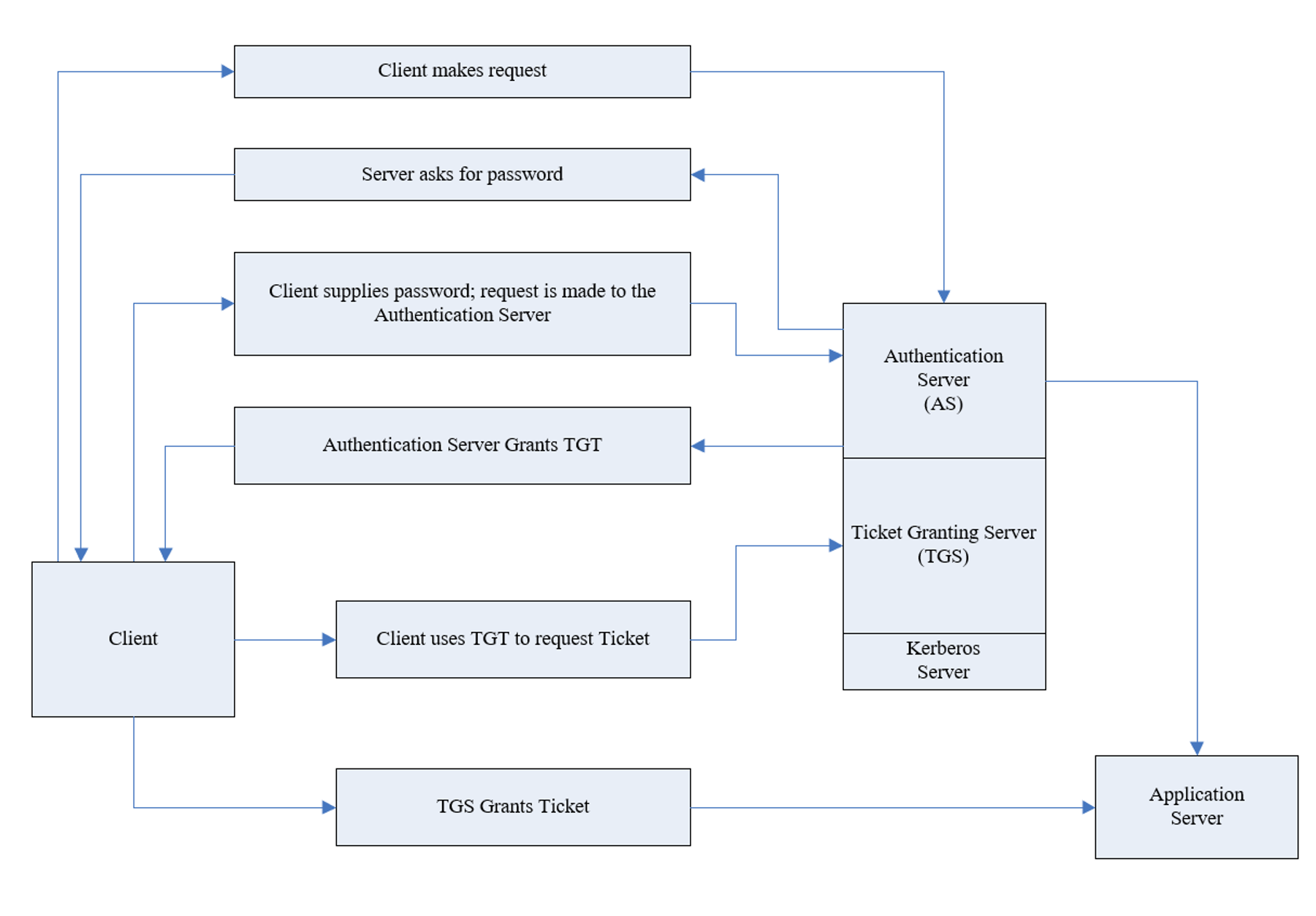
The Kerberos authentication process involves three main entities: the client, the Key Distribution Center (KDC), and the target server.
The KDC, integral to the AD domain controller, serves as a trusted third party in this process:
- Authentication Request: Initiated by the client for a Ticket Granting Ticket (TGT) from the KDC.
- TGT Issuance: Upon verifying the client’s credentials, the KDC issues a TGT, encrypted with the client’s secret key.
- Service Ticket Request: The client uses the TGT to request a service ticket for the desired server/service.
- Service Ticket Issuance: The KDC provides a service ticket, encrypted with the server’s secret key.
- Service Access: The client presents this ticket to the server, which, upon verification, grants the requested access.
Key Components
- Ticket Granting Ticket (TGT): Facilitates service ticket requests, encrypted with a KDC-known secret key.
- Service Ticket: Authorizes access to specific services, encrypted with the service’s secret key.
- Session Key: A temporary key for encrypted communication between the client and server.
Advantages in Active Directory
- Secure Authentication: Utilizes strong cryptography to protect against various attacks.
- Single Sign-On (SSO): Streamlines user access to multiple services post-authentication.
- Delegated Authentication: Enables secure credential delegation for accessing resources.
Attack Vectors on Kerberos Authentication
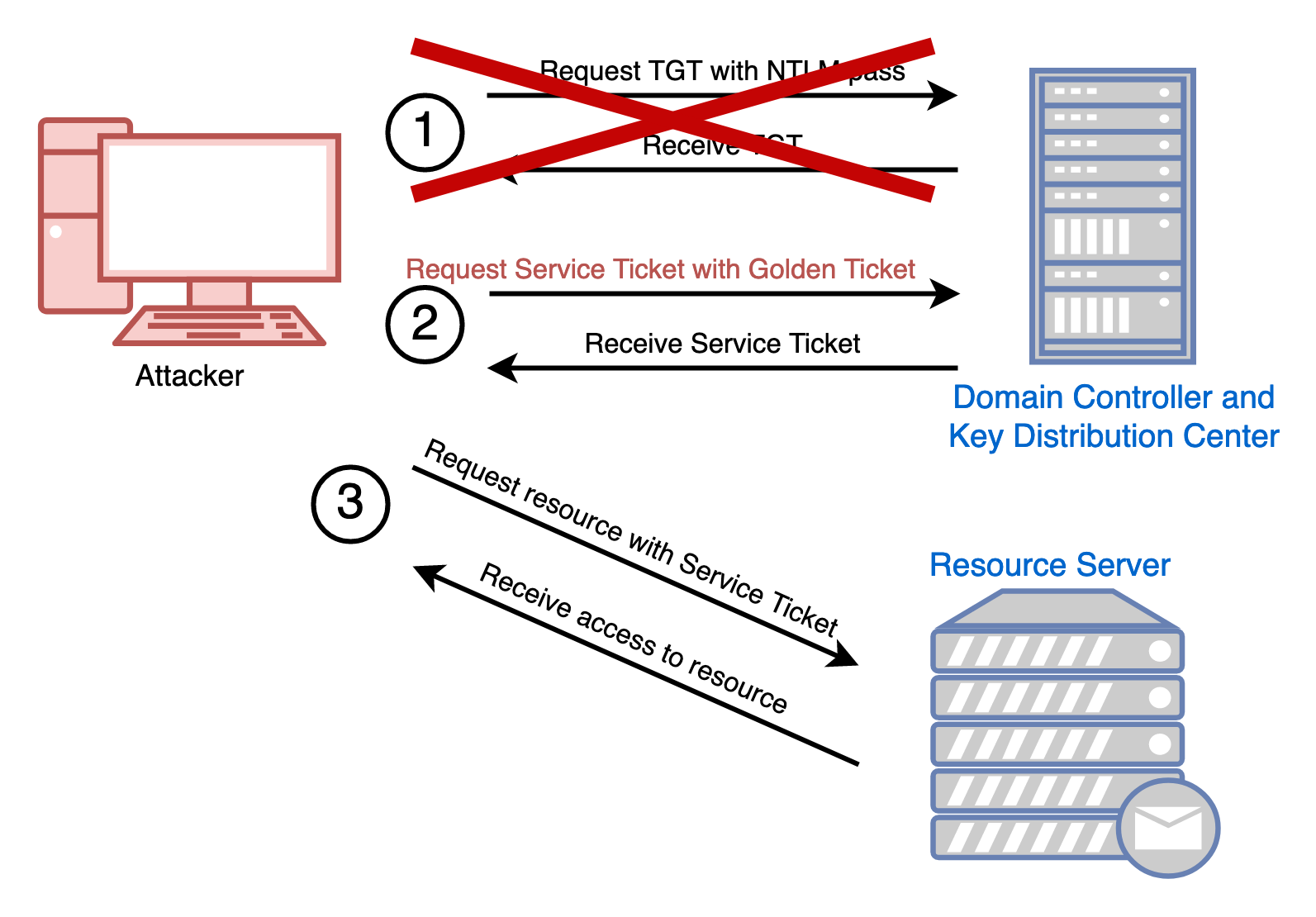
Golden Ticket Attack
The Golden Ticket attack involves an adversary gaining domain administrative privileges and subsequently accessing the Key Distribution Center’s (KDC) Ticket Granting Service (TGS) secret key.
With this key, they can create a Ticket Granting Ticket (TGT) for themselves, effectively granting unlimited access to any service within the AD domain.
This TGT is called “Golden Ticket” and allows the adversary to impersonate any user, access any service, and modify any data within the domain, often without detection for a significant period.
Silver Ticket Attack
The Silver Ticket attack is more targeted than the Golden Ticket attack. Instead of gaining access to all services within the AD, the adversary focuses on a specific service.
By compromising a service account, they can obtain the service’s secret key and forge a Service Ticket (ST) to that service without interacting with the KDC for a valid TGT.
This attack allows unauthorized access to specific services, such as file servers or databases, enabling data theft or manipulation without alerting the broader security mechanisms within the domain.
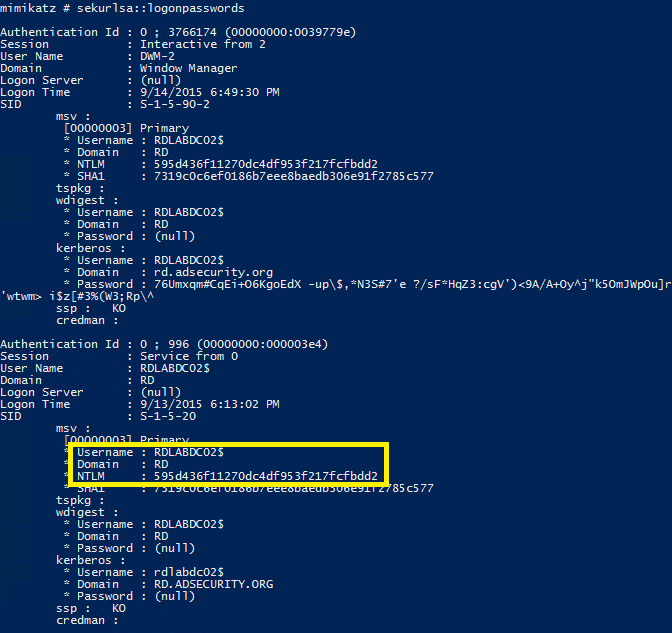
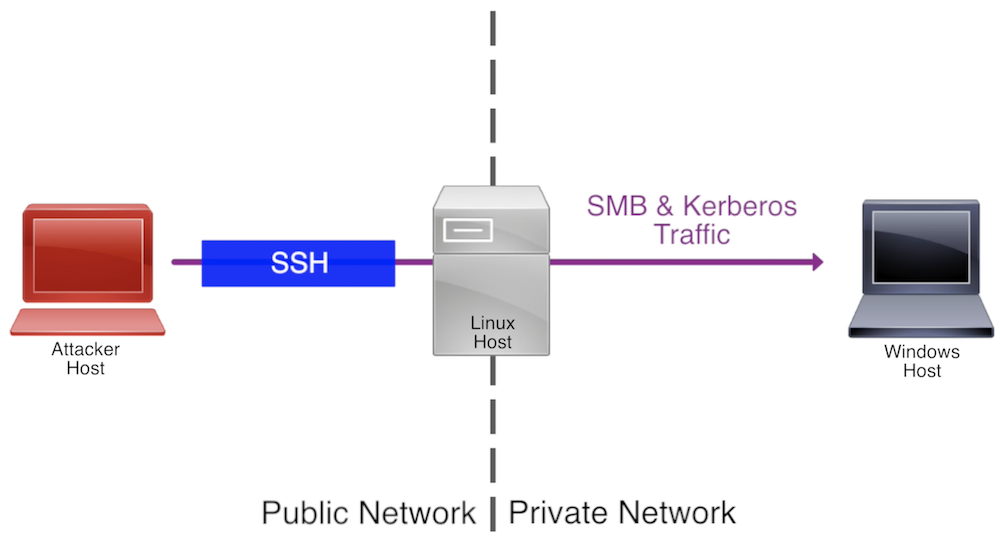
Pass the Ticket (PtT)
Pass the Ticket (PtT) involves the theft and reuse of legitimate Kerberos tickets.
Adversaries capture Kerberos tickets from authenticated users and then use those tickets to impersonate the user, gaining access to resources and services within the AD domain.
This attack bypasses the need for password theft or cracking, as the ticket itself serves as proof of identity.
Effective detection and mitigation require sophisticated network monitoring to identify anomalous use of Kerberos tickets.
Kerberoasting
Kerberoasting is an attack that abuses the Kerberos protocol to harvest password hashes for Active Directory user accounts with servicePrincipalName (SPN) values — i.e., service accounts.
A user is allowed to request a ticket-granting service (TGS) ticket for any SPN, and parts of the TGS may be encrypted with RC4 using the password hash of the service account that is assigned the requested SPN as the key.
Therefore, an adversary who is able to steal TGS tickets (either from memory or by capturing them by sniffing network traffic) can extract the service account’s password hash and attempt an offline brute force attack to obtain the plaintext password.
AS-REP Roasting
AS-REP Roasting targets accounts configured to not require Kerberos pre-authentication.
When enabled, a user requesting access to a resource initiates communication with the Domain Controller (DC) by sending an Authentication Server Request (AS-REQ) message with a timestamp that is encrypted with the hash of their password.
If and only if the DC is able to successfully decrypt the timestamp with the hash of the user’s password, it will then send an Authentication Server Response (AS-REP) message that contains the Ticket Granting Ticket (TGT) to the user.
Part of the AS-REP message is signed with the user’s password.
For each account found without pre-authentication, an adversary may send an AS-REQ message without the encrypted timestamp and receive an AS-REP message with TGT data which may be encrypted with an insecure algorithm such as RC4.
The recovered encrypted data may be vulnerable to offline password cracking attacks similarly to Kerberoasting and expose plaintext credentials.