Use-After-Free
What is Use-After-Free?
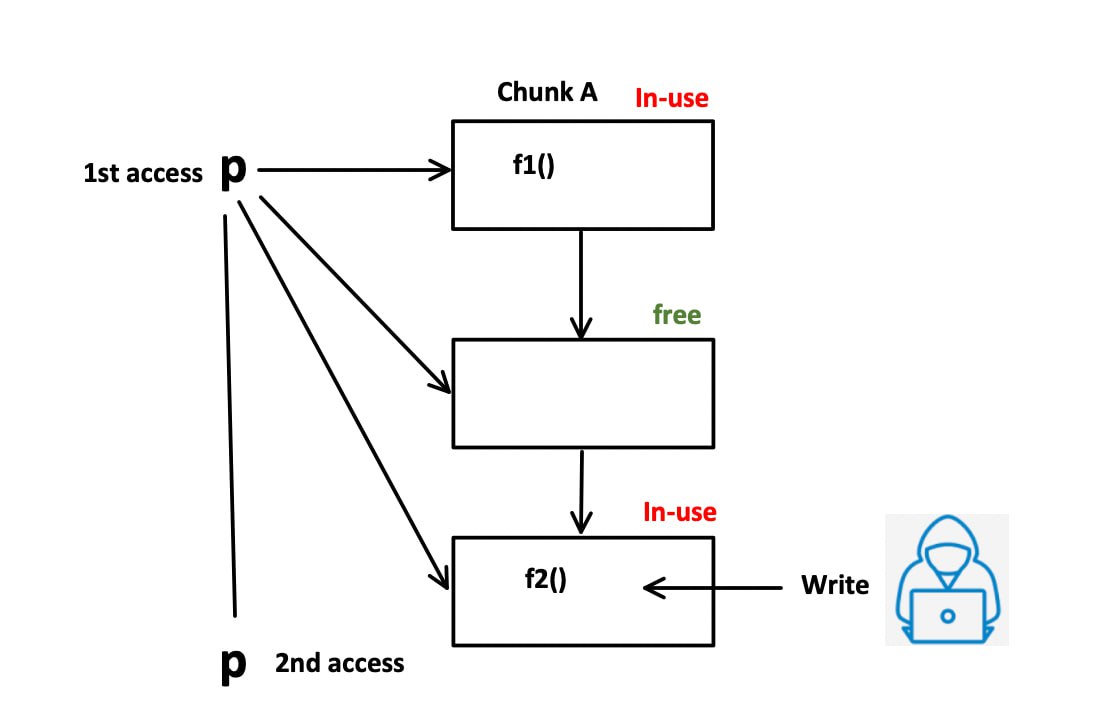
Use-After-Free (UAF) is a memory corruption vulnerability that occurs when a program continues to use a pointer after it has been freed. In simpler terms, UAF vulnerabilities arise when an object is deleted (or “freed”) in memory, but references to that object still exist and are later used.
How Does It Happen?
A typical UAF scenario follows this sequence:
- Allocation: Memory is allocated to store an object, often using functions like malloc() in C or new in C++.
- Use: The program uses that object for some operations.
- Deallocation: The memory used by the object is deallocated, or “freed”, often using functions like free() in C or delete in C++.
- Dangling Reference: The pointer to the object still exists, even though the object has been deleted.
- Reuse: The program tries to use the object through the dangling pointer, leading to undefined behavior.
1
2
3
4
5
6
7
8
9
10
11
12
#include <stdlib.h>
int main() {
char *ptr = malloc(10); // Step 1: Allocation
strcpy(ptr, "hello"); // Step 2: Use
free(ptr); // Step 3: Deallocation
// ... some other code ...
strcpy(ptr, "world"); // Step 5: Reuse (UAF)
}
Identification
Identifying UAF vulnerabilities often involves:
- Code Auditing: Manually reviewing source code to identify instances where a pointer is used after being freed.
- Dynamic Analysis Tools: Using tools like AddressSanitizer, Valgrind, or custom fuzzers to catch UAFs during runtime.
- Static Analysis Tools: Utilizing static code analyzers that can flag potential UAF vulnerabilities.
Exploitation
Exploiting UAF vulnerabilities can allow an adversary to:
- Execute arbitrary code
- Leak sensitive information
- Gain unauthorized access or privileges
Techniques for Exploitation:
- Heap Feng Shui: Manipulating heap layout to control what data replaces the freed object.
- Object-Oriented Programming (OOP) Abuse: Taking advantage of virtual function tables (vtables) to redirect program execution.
Mitigation
- Memory-safe languages: Using languages like Rust or Python that manage memory safely can mitigate the risk.
- Defensive Coding Practices: Always setting pointers to NULL after freeing them can prevent accidental reuse.
- Exploit Mitigations: Employ exploit mitigation techniques like Control Flow Integrity (CFI) and Address Space Layout Randomization (ASLR).
Special Considerations
- Real-time Systems: In embedded systems or automotive systems, the overhead of security checks may not be acceptable.
- IoT Devices: Such devices often have limited computational resources, making advanced mitigation techniques difficult to implement.
This post is licensed under CC BY 4.0 by the author.